CyberLock is a key-centric access control system designed to increase security, accountability, and key control throughout your organization. Based on a unique design of electronic lock cylinders and programmable smart keys, CyberLock solves security problems that no other system can.
COMPONENTS OF THE CYBERLOCK SYSTEM
- Locks: CyberLock cylinders are high security electronic locks designed to track and control access throughout your facility. Cylinders are designed to the exact dimensions of the mechanical lock cylinders they replace. As the CyberLock cylinder needs no power or wiring for installation, it is ideal for securing remote and mobile assets
2. Keys: CyberLock smart keys are programmed with access permissions for each key holder, they serve as the gatekeeper for the CyberLock system. Each key contains a specific list of authorized locks and schedules of when they may be accessed. In addition, they provide the power needed to energize the CyberLock cylinder.
3. Communicators: Communicators serve as the interface between CyberLock hardware and CyberAudit management software. Through a communicator, key information is downloaded into the software and new schedules and permissions are uploaded into the keys.
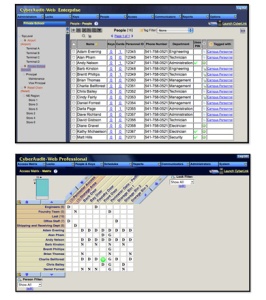
4. CyberAudit Management Software: CyberAudit is the software suite for management of CyberLock systems of all sizes. The software allows you to assign keys, set expirations, add new cylinders, monitor staff and contractors, create access schedules, and generate audit trails & custom reports.
HOW THE CYBERLOCK SYSTEM WORKS
Step 1 – Install Your High Security Locks: Replace existing mechanical cylinders with CyberLock electronic cylinders. Each CyberLock cylinder is an electronic version of a standard mechanical lock cylinder. Installation requires no wiring, and the cylinder does not contain a battery, simply remove the existing mechanical cylinder and replace it with a CyberLock cylinder.
Step 2 – Program Your Electronic Keys: Assign CyberKey smart keys to users. CyberKey smart keys are programmed with access privileges for each user and contain a list of locks the user may open with a schedule of days and times they are allowed access. For instance, a key can be programmed to allow access from 8 a.m. to 6 p.m. on weekdays and 10 a.m. to 4 p.m. on Saturdays. It can also be programmed to expire on a specific date at a specific time for increased security.
Step 3 – Open Your High Security Locks: When a CyberKey meets a CyberLock, the cylinder is energized and an information exchange occurs to determine if the key has access to that specific lock cylinder. If authorized, the lock will open. Both the lock and key record all access events, including access granted and unauthorized access attempts.
Step 4 – Gather Your Audit Trail: When a key is presented to a communication device, the key’s audit trail is downloaded and new access privileges are uploaded. Expiring keys frequently ensures users regularly update their keys. An expired key will not work until it is updated.
Step 5 – View Your Audit Trail: The CyberLock system is managed through CyberAudit management software. Customized audit reports and periodic notifications on suspicious activities can be automatically generated via email.
WHY CYBERLOCK?
- Versatility – Control Access to Every Asset: CyberLock cylinders are easily deployed not only on doors, but also on gates, trucks, shipping containers, and other mobile and remote assets. Full access control is now possible on assets previously restricted to only mechanical locks and keys.
- Cost Effective – Eliminate Expensive Cabling: Electronic cylinders are installed without power or wiring making setup and installation quick, easy, and affordable. The batteries in the CyberKey smart keys energize the CyberLock cylinders, bypassing the need to install and maintain expensive wiring.
- Superior Key Control -Re-Key Electronically: Keys are programmed with access permissions for each individual user. If a key is lost, it can easily be deactivated in the system, eliminating the need to re-key.